Introduction: KhadashPay V3.5
KhadashPay is an easy-to-use DIY payment system that enables business owners to set up a card payment system in their store without the need to buy an expensive terminal, pay fees for each transaction, and waste time and resources dealing with the bank.
As a customer of the store where KhadashPay is employed, you can know for sure that KhadashPay does not keep any logs and doesn't require a bit of your personal information to create an account.
The name KhadashPay consists of two parts: Khadash (which means "new" in Hebrew) and Pay.
Before you continue reading this instructable, please note that this payment system is not connected to any existing financial institution and operates completely offline. All the "money" kept in it is nothing more than just numbers entered by the operator, encrypted by the 3DES + AES + Blowfish + Serpent encryption algorithm In CBC mode, and stored on an SD card.
Supplies
- ESP32 x1
- 2.4 Inch TFT LCD with ILI9341 x1
- Mifare RC522 RFID Reader x1
- RFID cards x4
- MH-SD Card Module x1
- SD Card x1
- 4x4 Keypad x1
- Arduino Nano x1
- 4.7k resistors x2
- PS/2 Keyboard x1 *optional
- PS/2 Port x1 *optional
- 10µF capacitor x1 *optional
Step 1: How It Came to Be
KhadahPay V3.5 is my attempt to combine the best aspects of KhadashPay V3.0 and KhadashPay V2.0 (Raspberry Pi Pico Version) while also addressing the keypad issue present in the KhadashPay V3.0.
To do this, I've ported the vault capability from the KhadashPay V2.0 (Raspberry Pi Pico Version) and added Arduino to handle the 4x4 keypad.
To make your interaction with the KhadashPay V3.5 more comfortable, you can connect a PS/2 keyboard to it.
Step 2: 3DES + AES + Blowfish + Serpent Encryption Algorithm in CBC Mode
The "3DES + AES + Blowfish + Serpent" encryption algorithm in cipher block chaining mode first appeared in the Midbar V2.5. And since then has been utilized by the Midbar (Raspberry Pi Pico Version), Midbar V3.0, Midbar V4.0, KhadashPay V2.0, Midbar (Raspberry Pi Pico Version) V2.0, KhadashPay V2.0 (Raspberry Pi Pico Version), Midbar V5.0, Midbar (STM32F401CCU6 Version), KhadashPay V3.0 (STM32F401CCU6 Version), KhadashPay V3.0, and Midbar (STM32F401CCU6 + Arduino Uno Version).
Although the "3DES + AES + Blowfish + Serpent" encryption algorithm ain't exactly what I would call "a cryptographically weak encryption algorithm," operating it in a weird derivation of the ECB mode, the way it was done by the Midbar V2.0 wasn't the best idea that I had. Even though that wouldn't've allowed the attacker to produce the legitimate ciphertext by swapping the blocks within the ciphertext, an attacker could still make a legitimate ciphertext by replacing the nth block of the ciphertext N1 with the nth block of the ciphertext N2. To fix that vulnerability (instead of just notifying the user that the decrypted ciphertext might've been forged), I made the "3DES + AES + Blowfish + Serpent" encryption algorithm work in CBC mode. So, if an attacker replaces a block of ciphertext, they spoil not just that block but also the subsequent one.
I'll be honest with you, the bit-flipping attack "kinda works," but I doubt that it would ever go unnoticed because of the "HMAC-SHA256"-based integrity verification feature
And let's not forget that this encryption algorithm performs the operation called superencryption.
As defined by NIST, superencryption is an encryption operation for which the plaintext input to be transformed is the ciphertext output of a previous encryption operation.
Such organization of the encryption algorithms makes a combined encryption algorithm that is at least as strong as the strongest one in the cascade, has a longer key, might be more resistant to some attacks, and might produce a ciphertext with higher entropy. Anyway. It won't hurt to have an additional layer of security (or several of them).
Step 3: Integrity Verification
Another cool feature provided to you by KhadashPay is the "HMAC-SHA256"-based integrity verification.
Before encrypting the user data, KhadashPay computes the tag for that data and encrypts it alongside data.
Later on, when KhadashPay decrypts your data, it also decrypts the previously calculated tag and computes a new tag for the newly decrypted data. It then compares both tags. If they don't match - KhadashPay will promptly notify you that the integrity verification has failed.
Step 4: "Belonging Check"
Even though KhadashPay can't decrypt user data without the user's card, I still decided to add an additional check, just in case.
The so-called "Belonging Check" (didn't really know what else to call it) is a feature that allows the KhadashPay to verify whether the record with the balance belongs to the card that is taped on the RFID reader or not.
Step 5: Install CP210x Driver and Configure Arduino IDE *Optional
If you've never flashed ESP32 before you need to configure Arduino IDE and install CP210x driver to upload the firmware into the board, you can download the CP210x driver for ESP32 here: https://www.silabs.com/developers/usb-to-uart-bridge-vcp-drivers
Configuring IDE isn't a part of this tutorial. You can read about it here: https://randomnerdtutorials.com/installing-the-esp32-board-in-arduino-ide-windows-instructions/
Step 6: Download Firmware
You can download the firmware for KhadashPay from one of these sources.
SourceForge: https://sourceforge.net/projects/khadashpay/
OSDN: https://osdn.net/projects/khadashpay/
GitHub: https://github.com/Northstrix/KhadashPay
If you just need the firmware for the device alongside the RNG, then I would advise you to download the archive that weighs less than 2Mb either from SourceForge or OSDN.
But if you need the firmware for all versions of KhadashPay alongside the extra code, photos, and diagrams, in that case, I would advise you to download the 146 MB archive from GitHub.
Step 7: Download and Install the Libraries
TFT_eSPI: https://github.com/Bodmer/TFT_eSPI
rfid: https://github.com/miguelbalboa/rfid
Keypad: https://github.com/Chris--A/Keypad
ps2dev: https://github.com/Harvie/ps2dev
PS2KeyAdvanced: https://github.com/techpaul/PS2KeyAdvanced
PS2KeyMap: https://github.com/techpaul/PS2KeyMap
The process of unpacking libraries is typical. You can unpack the content of the archive into the folder: ...\Arduino\libraries. Or open the Arduino IDE, click to the Sketch -> Include Library -> Add .ZIP Library... and select every archive with libraries.
Other required libraries are already present in one way or another.
Step 8: Replace the Preset File for the TFT_eSPI Library
TFT_eSPI Library requires the config to be adjusted depending on the display and the board that drives that display. Initially, I wanted to write the mini-guide on adjusting the config for the ILI9341 display to be properly used on the ESP32's HSPI. But then I realized that it would be more convenient to attach the adjusted config to the firmware and tell you where to place it.
Take the "User_Setup.h" file from the "V3.5\ESP32_Version" folder and place it in the "C:\Program Files (x86)\Arduino\libraries\TFT_eSPI-master" folder.
Step 9: Switch the Partition Scheme to the "Huge APP (3MB No OTA/1MB SPIFFS)"
You have to switch the partition scheme to the "Huge APP (3MB No OTA/1MB SPIFFS)" before you continue working with ESP32 because the firmware for the vault is too big for the default partition.
Step 10: Generate Keys
To make the unauthorized deciphering of your data computationally infeasible - It is crucial to generate your own keys and never reuse them
It's entirely up to you how to generate the keys. I can only offer you an option to do so.
I've modified one of my previous projects to work as a random number generator, the generated output seems "random enough" for me, but I haven't run any tests. So, I can't guarantee that it's random.
Use it at your own risk!
To generate the keys - launch gen.exe from the "V3.5\ESP32_Version\Untested RNG" folder and click the "Generate keys for KhadashPay V3.5" button. The background turns from dark gray to light gray when you press that button.
Step 11: Modify the Firmware
Open the "Firmware.ino" file from the "V3.5\ESP32_Version\Firmware" folder and replace my keys with those you've generated.
Regarding the password vault part of the KhadashPay V3.5, you can change the number of available slots for your logins by modifying the "#define MAX_NUM_OF_RECS" line. You can store as many logins as you want on this device as long as there is enough space available on the SD card.
Step 12: Flash ESP32
Upload the firmware from the "V3.5\ESP32_Version\Firmware_for_ESP32" folder into the ESP32. Don't forget to hold the "BOOT" button when the firmware upload starts.
Some boards will flash without any problems.
Unfortunately, that's not the case for all boards. If you configured IDE correctly, installed drivers, selected the corresponding port, and still keep getting this error: A fatal error occurred: Failed to connect to ESP32: Timed out waiting for packet header. Connect a 10µF capacitor to the board while flashing.
Connect the positive lead of the capacitor to the EN pin of the ESP32;
Connect the negative lead of the capacitor (usually indicated by the gray stripe) to the GND pin of the ESP32.
Don't forget to disconnect the capacitor after the board flashes.
Step 13: Flash Arduino
Upload the firmware from the "V3.5\ESP32_Version\Firmware_for_Arduino" folder into the Arduino.
Step 14: Assemble the Device
In my opinion, assembling KhadashPay V3.5 is comparable in difficulty to Midbar (STM32F401CCU6 + Arduino Uno Version).
As for the possible component replacements, you can replace 4.7k resistors with 1k - 4.7k resistors.
Step 15: Power the KhadashPay Up
Just like the Midbar V5.0, KhadashPay V3.5 has twelve lock screens. KhadashPay V3.5 randomly chooses the lock screen at startup.
After the KhadashPay has chosen the lock screen, it displays the "חדשפיי" inscription with the shifting background and the "Tap RFID card N1" inscription on the bottom of the lock screen.
*Credit for photos:
Photo by MJ Tangonan on Unsplash
Photo by Piotr Chrobot on Unsplash
Photo by Zac Gudakov on Unsplash
Photo by Kevin Bree on Unsplash
Photo by Igor Flek on Unsplash
Photo by Justice Hubane on Unsplash
Photo by Robert Bye on Unsplash
Image by JORGE TAPIA from Pixabay
Photo by Daniel McCullough on Unsplash
Photo by Michael Beener on Unsplash
Step 16: Tap Four RFID Cards on the RFID Reader
After you've powered the device up, tap four RFID cards on the RFID reader one after another. The most important thing here is to tap the cards in the same order every time you unlock KhadashPay. Otherwise, it just won't unlock.
If you don't have four cards, you can tap one card four times.
And by the way, the first card you tap on the RFID reader becomes the "operator card" right after you set the master password. You'll need this information later in this tutorial. For now, just remember it.
Step 17: Set the Master Password
To use the KhadashPay, you first need to set the master password.
While entering the master password on the 4x4 keypad, note that the '*' key serves as a backspace.
And remember that you can't change the master password without losing the ability to decrypt all user data stored on the SD card!
KhadashPay won't be able to decrypt the user data without the master password because the keys for the encryption algorithms are partially derived from it. Perhaps, it won't even unlock without the correct master password.
When you're done entering the master password, press either the '#" or 'C' key on the keypad to finish the input and set the master password.
After you've unlocked the KhadashPay and got to the menu:
- Press the "0" key on the 4x4 keypad to go down the menu;
- Press the "8" key on the 4x4 keypad to go up the menu;
- Press the "#" key on the 4x4 keypad to perform the selected action;
- Press the '.' key on the 4x4 keypad to show the random lock screen. After that, press any key to return to the menu.
Step 18: Create an Account
Ok, let's start with the facts about the KhadashPay account.
- Each account is bound to the RFID card and PIN;
- The PIN can have a length from 1 to 8 characters;
- The PIN can have the following characters: '0', '1', '2', '3', '4', '5', '6', '7', '8', '9', '.', 'B', 'D';
- A client can create several accounts using the same card as long as the pins are different;
- The maximum amount of money stored in the account is only limited by the double variable type (don't worry about that, the KhadashPay can still store a 15-digit number without any problems);
- Not even the owner of the KhadashPay can see your balance without your card.
To create an account on KhadashPay V3.5:
Operator:
- Select the "New Account" line in the menu;
- Press the '#' key on the 4x4 keypad;
- Tap the operator RFID card on the RFID reader;
- Press the '#' key on the 4x4 keypad and give the device to the client.
Client:
- Tap your RFID card on the RFID reader;
- Set your PIN;
- Press the '#' key on the 4x4 keypad;
- Enter the PIN that you've set again;
- Press the '#' key on the 4x4 keypad.
Step 19: Put Money Into the Account
To put money into the account:
Operator:
- Select the "Put Money In" line in the menu;
- Press the '#' key on the 4x4 keypad;
- Tap the operator RFID card on the RFID reader;
- Enter the amount of money to be put into the client's account;
- Press the '#' key on the 4x4 keypad;
- Press the '#' key on the 4x4 keypad and give the device to the client.
Client:
- Tap your RFID card on the RFID reader;
- Enter your PIN;
- Press the '#' key on the 4x4 keypad.
Step 20: Make a Sale
To make a sale:
Operator:
- Select the "Make A Sale" line in the menu;
- Press the '#' key on the 4x4 keypad;
- Tap the operator RFID card on the RFID reader;
- Enter the sale amount;
- Press the '#' key on the 4x4 keypad;
- Press the '#' key on the 4x4 keypad and give the device to the client.
Client:
- Tap your RFID card on the RFID reader;
- Enter your PIN;
- Press the '#' key on the 4x4 keypad.
Step 21: View Balance
To view balance:
Operator:
- Select the "View Balance" line in the menu;
- Press the '#' key on the 4x4 keypad;
- Tap the operator RFID card on the RFID reader;
- Press the '#' key on the 4x4 keypad and give the device to the client.
Client:
- Tap your RFID card on the RFID reader;
- Enter your PIN;
- Press the '#' key on the 4x4 keypad.
Step 22: Connect PS/2 Keyboard to KhadashPay
After exploring the payment system capabilities of the KhadashPay V3.5, it's time for you to explore the vault capabilities.
Connect a PS/2 keyboard for a better user experience.
Step 23: Add Login
To add a login using the PS/2 keyboard:
- Select the "Other Options" line in the main menu;
- Press "Enter" on the PS/2 keyboard;
- Tap the operator RFID card on the RFID reader;
- Select the "Logins" line;
- Press "Enter" on the PS/2 keyboard;
- Select the "Add" line;
- Press "Enter" on the PS/2 keyboard;
- Choose the slot into which you want to put the login to by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the PS/2 keyboard;
- Press "Enter" on the PS/2 keyboard;
- Select the "PS/2 Keyboard" line;
- Press "Enter" on the PS/2 keyboard;
- Enter the title;
- Press "Enter" on the PS/2 keyboard;
- Enter the username;
- Press "Enter" on the PS/2 keyboard;
- Enter the password;
- Press "Enter" on the PS/2 keyboard;
- Enter the website;
- Press "Enter" on the PS/2 keyboard.
According to the tests I've conducted - ESP32 can encrypt and decrypt a 650-character long string without any problems using the 3DES + AES + Blowfish + Serpent encryption algorithm. So, technically, you can put 650 characters into a field of a record.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
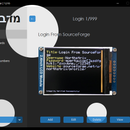
Step 24: View Login
To view a login:
- Select the "Other Options" line in the main menu;
- Press "Enter" on the PS/2 keyboard;
- Tap the operator RFID card on the RFID reader;
- Select the "Logins" line;
- Press "Enter" on the PS/2 keyboard;
- Select the "View" line;
- Press "Enter" on the PS/2 keyboard;
- Choose the slot from which you want to view the login by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the PS/2 keyboard;
- Press "Enter" on the PS/2 keyboard;
- Press the "Tab" key on the PS/2 keyboard to print the record to the serial terminal.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 25: Edit Login
To edit a login:
- Select the "Other Options" line in the main menu;
- Press "Enter" on the PS/2 keyboard;
- Tap the operator RFID card on the RFID reader;
- Select the "Logins" line in the main menu;
- Press "Enter" on the PS/2 keyboard;
- Select the "Edit" line;
- Press "Enter" on the PS/2 keyboard;
- Select the login you would like to edit by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the PS/2 keyboard;
- Press "Enter" on the PS/2 keyboard;
- Select the input source;
- Press "Enter" on the PS/2 keyboard;
- Depending on the chosen input source, either enter the new password on the PS/2 keyboard or paste it to the Serial Terminal;
- Depending on the chosen input source, either press "Enter" on the PS/2 keyboard or press the "Send" button in the Serial Terminal.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 26: Delete Login
To delete a login:
- Select the "Other Options" line in the main menu;
- Press "Enter" on the PS/2 keyboard;
- Tap the operator RFID card on the RFID reader;
- Select the "Logins" line;
- Press "Enter" on the PS/2 keyboard;
- Select the "Delete" line;
- Press "Enter" on the PS/2 keyboard;
- Select the login you would like to delete by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the PS/2 keyboard;
- Press "Enter" on the PS/2 keyboard.
Step 27: Find a Good Use for KhadashPay
After spending a considerable amount of time and effort developing the KhadashPay, I'm thrilled to announce that I have finally created a version of KhadashPay that I believe is good enough to be deployed in your store.
It doesn't have the keypad issue present in the KhadashPay V3.0, and it is the first version of KhadashPay that can work with both the PS/2 keyboard and the 4x4 keypad.
Moreover, KhadashPay V3.5 also utilizes the password vault capability from KhadashPay V2.0 (Raspberry Pi Pico Version). So, you can use it to securely store your logins as well.
It's also worth mentioning that KhadashPay's source code is distributed under the MIT license. That grants you the freedom to customize and modify KhadashPay according to your preferences. The scope of what you can do with KhadashPay, and what you can change in it is vast, so if you want to make your own version of KhadashPay or change something in it, don't wait for anyone else to do it for you. Take the initiative into your own hands and make any necessary changes as you see fit.
If you found this tutorial to be useful, please consider sharing it.
Thank you for reading this tutorial.