Introduction: DIY Hardware Data Vault With Teensy 4.1 (Midbar (Teensy 4.1) V3.0)
Established password managers are easy to set up, convenient to use, and utilize advanced cryptography to protect your data. However, all password managers share the same vulnerability - they are not the only program that runs on your computer. Your computer may have thousands of other processes running alongside the password manager, and some of these processes can be malicious. These processes can render the whole cryptographic backbone of the password manager useless by simply bypassing it.
In my opinion, the best solution to that problem is to run a password manager on a dedicated hardware that runs no "alien" processes on it.
One such solution is demonstrated in this tutorial.
Supplies
- Teensy 4.1 x1
- 1.77 Inch TFT LCD with ST7735 x1
- USB Keyboard x1
- USB 2.0 Port (I took it from the panel expansion bracket) x1
- Micro SD Card *optional x1
Step 1: Why Midbar?
Midbar (מדבר) is a Hebrew word that means "pasture," "uninhabited land," "wilderness," "large tracts of wilderness (around cities)," and "desert." I had two reasons for choosing the word Midbar as the name of this project. First - while working on my previous projects, I noticed that the so-called "device that keeps your personal data secure in an encrypted form" market is pretty much a "desert around the oasis of the password manager market." Second - I couldn't find a better word to describe this project. At first, I wanted to call it a "Password Vault," but it's more than that. So, I decided to call it Midbar.
Step 2: EEPROM Partitioning
The Midbar (Teensy 4.1 Version) V3.0 enables you to securely store up to 16 login credentials and 12 credit card details in Teensy's internal memory. If that's not enough for you, don't worry, you can store hundreds of records on an SD card.
Step 3: EEPROM Integrity Check
Since there's not that much space available in EEPROM, I've decided to use a single IV for a record stored in the EEPROM and to verify the integrity of the whole EEPROM area utilized by the Midbar (Teensy 4.1 Version) V3.0 instead of individually verifying the integrity of each record, the way it's done for the records stored on the SD card.
Step 4: 3DES + AES + Blowfish + Serpent in CBC Mode
The "3DES + AES + Blowfish + Serpent" encryption algorithm in cipher block chaining mode first appeared in the Midbar V2.5. And since then has been utilized by the Midbar (Raspberry Pi Pico Version), Midbar V3.0, Midbar V4.0, KhadashPay V2.0, Midbar (Raspberry Pi Pico Version) V2.0, KhadashPay V2.0 (Raspberry Pi Pico Version), Midbar V5.0, Midbar (STM32F401CCU6 Version), KhadashPay V3.0 (STM32F401CCU6 Version), KhadashPay V3.0, Midbar (STM32F401CCU6 + Arduino Uno Version), KhadashPay V3.5, Black Swan V2.0, Midbar (Teensy 4.1 Version), Hash Latch, Midbar (Teensy 4.1 Version) V2.0, Midbar (ESP8266 Version) V2.0, Midbar (STM32F407VET6 Version), Midbar (STM32F407VET6 + Arduino Uno Version), DIY IoT Data Vault With Google Firebase (Midbar Firebase Edition V1.0), DIY IoT Payment System With Google Firebase (KhadashPay Firebase Edition V1.0), Midbar (STM32F407VET6 Version) V2.0, and Midbar V6.0.
Although the "3DES + AES + Blowfish + Serpent" encryption algorithm ain't exactly what I would call "a cryptographically weak encryption algorithm," operating it in a weird derivation of the ECB mode, the way it was done by the Midbar V2.0 wasn't the best idea that I had. Even though that wouldn't've allowed the attacker to produce the legitimate ciphertext by swapping the blocks within the ciphertext, an attacker could still make a legitimate ciphertext by replacing the nth block of the ciphertext N1 with the nth block of the ciphertext N2. To fix that vulnerability (instead of just notifying the user that the decrypted ciphertext might've been forged), I made the "3DES + AES + Blowfish + Serpent" encryption algorithm work in CBC mode. So, if an attacker replaces a block of ciphertext, they spoil not just that block but also the subsequent one.
I'll be honest with you, the bit-flipping attack "kinda works," but I doubt that it would ever go unnoticed because of the "HMAC-SHA256"-based integrity verification feature
And let's not forget that this encryption algorithm performs the operation called superencryption.
As defined by NIST, superencryption is an encryption operation for which the plaintext input to be transformed is the ciphertext output of a previous encryption operation.
Such organization of the encryption algorithms makes a combined encryption algorithm that is at least as strong as the strongest one in the cascade, has a longer key, might be more resistant to some attacks, and might produce a ciphertext with higher entropy. Anyway. It won't hurt to have an additional layer of security (or several of them).
*Note that when using the "3DES + AES + Blowfish + Serpent In CBC Mode" encryption algorithm to encrypt data stored on an SD card, it takes 10 bytes of plaintext and 6 random bytes and produces 16 bytes of ciphertext. The same scheme applies when calling this algorithm from the "Encryption Algorithms" menu. On the other hand, it takes 16 bytes of plaintext and produces 16 bytes of ciphertext when it encrypts data stored in EEPROM.
Step 5: Integrity Verification (for Data Stored on SD Card)
The Midbar (Teensy 4.1 Version) V3.0 is the eighteenth version of Midbar that verifies the integrity of the whole record. So, the legitimate ciphertexts moved between the cells aren't much of a threat to it.
The integrity verification feature of Midbar is based on "HMAC-SHA256." When you enter data into Midbar, it consolidates all the data into a single string, computes a tag for that string, and saves the newly computed tag in encrypted form. When you decrypt your data, Midbar also decrypts the previously saved tag and computes a new one for the decrypted data. It then compares both tags. If they don't match - Midbar notifies you that the integrity verification failed.
Step 6: Prepare the Software
You need to install the Arduino IDE and Teensyduino to flash Teensy 4.1.
For more information on that, please refer to: https://www.pjrc.com/teensy/td_download.html
Step 7: Download Firmware
You can download the firmware for Midbar from one of these sources.
SourceForge: https://sourceforge.net/projects/midbar/
GitHub: https://github.com/Northstrix/Midbar
If you just need the firmware for the device alongside the RNG, then I would advise you to download a 3.4 MB archive from SourceForge.
But if you need the firmware for all versions of Midbar alongside the extra code, photos, and diagrams, in that case, I would advise you to download the 323 MB archive from GitHub.
Step 8: Download and Install the Libraries
Adafruit-GFX-Library: https://github.com/adafruit/Adafruit-GFX-Library
Adafruit_BusIO: https://github.com/adafruit/Adafruit_BusIO
Adafruit-ST7735-Library: https://github.com/adafruit/Adafruit-ST7735-Library
The process of unpacking libraries is typical. You can unpack the content of the archive into the folder: ...\Arduino\libraries. Or open the Arduino IDE, click to the Sketch -> Include Library -> Add .ZIP Library... and select every archive with libraries.
Other required libraries are already present in one way or another.
Step 9: Clear EEPROM
To use Midbar, you first need to clear EEPROM.
To do so, upload the firmware from the "Teensy 4.1 Version\V3.0\Clear_EEPROM" folder into Teensy 4.1.
Step 10: Generate Keys
To make the unauthorized deciphering of your data computationally infeasible - It is crucial to generate your own keys and never reuse them
It's entirely up to you how to generate the keys. I can only offer you an option to do so.
I've modified one of my previous projects to work as a random number generator, the generated output seems "random enough" for me, but I haven't run any tests. So, I can't guarantee that it's random.
Use it at your own risk!
To generate the keys for Midbar - launch gen.exe from the "Teensy 4.1 Version\V3.0\Untested RNG" folder and click the "Gen. keys for Midbar (Teensy 4.1) V3.0" button. The background turns from dark gray to light gray when you press that button.
Step 11: Modify Firmware
Open the "Firmware.ino" file from the "Teensy 4.1 Version\V3.0\Firmware" folder, and then replace my keys with those you've generated.
You can also tweak some parameters in the following lines:
#define MAX_NUM_OF_RECS 999
// Max. number of chars for each filed for the logins stored in EEPROM
#define MAX_NUM_OF_CHARS_FOR_USERNAME 52
#define MAX_NUM_OF_CHARS_FOR_PASSWORD 52
#define MAX_NUM_OF_CHARS_FOR_WEBSITE 56
// You can repartition the field sizes as long as the sum of all three values is 160
// Max. number of chars for each filed for the credit cards stored in EEPROM
#define MAX_NUM_OF_CHARS_FOR_CARDHOLDER 39
#define MAX_NUM_OF_CHARS_FOR_CARD_NUMBER 20
#define MAX_NUM_OF_CHARS_FOR_EXPIRATION_DATE 16
#define MAX_NUM_OF_CHARS_FOR_CVN 3
#define MAX_NUM_OF_CHARS_FOR_PIN 8
#define MAX_NUM_OF_CHARS_FOR_ZIP_CODE 10
// You can repartition the field sizes as long as the sum of all values is 96
uint16_t colors[4] = { // Purple, Yellow, Green, Blue
0xb81c, 0xfde0, 0x87a0, 0x041c
};
const uint16_t current_inact_clr = colors[3];
const uint16_t stripe_on_the_right_and_oth_opts_color = colors[0];
const uint16_t five_six_five_red_color = 0xf940;
Step 12: Upload the Modified Firmware Into Teensy 4.1
Upload the modified firmware from the "Teensy 4.1 Version\V3.0\Firmware" folder into Teensy 4.1.
Don't forget to set the value of the "USB Type" line to the "Serial + Keyboard + Mouse + Joystick."
Step 13: Assemble Midbar
Assemble the circuit and insert a Micro SD card formatted to the FAT32 filesystem into the Teensy's built-in SD card slot. When it comes to the "BL" pin of the ILI9341 display, different versions of the display have different requirements on what to do with it. Some versions specify that it must be connected to the +3.3V, some require it to be grounded, and others allow you to leave it unconnected.
According to the PJRC official website, the digital pins of Teensy 4.1 are not 5V tolerant. Because of that, I would strongly advise you to double-check that you have not mistakenly connected anything, apart from the USB 2.0 Port to the "5V" pin.
Step 14: Power the Midbar Up
After being powered up, the Midbar displays the "Midbar Teensy 4.1" and "Press Any Key" inscriptions alongside the lock screen.
*Credit for the photos:
Photo by Kevin Hernandez on Unsplash
Photo by Ahmad Mohammed on Unsplash
Step 15: Set Master Password
To use the Midbar, you first need to set the master password.
You can't change your master password without performing the factory reset first!
Midbar won't be able to decrypt your data without your master password because the keys for the encryption algorithms are partially derived from it. Perhaps it won't even unlock without the correct master password.
When you're done entering your master password, press either the "Enter" or the "ESC" key on the USB keyboard.
After you've unlocked the vault and got to the main menu:
- Press the "↓" (DOWNWARDS ARROW) key on the USB keyboard to go down the menu.
- Press the "↑" (UPWARDS ARROW) key on the USB keyboard to go up the menu.
- Press either the "Enter" key on the USB keyboard to open the selected menu.
- While in the submenu, press either the "Esc" or the "Backspace" key on the USB keyboard to return to the main menu.
While entering a text in a tab:
- Press "Enter" on the USB keyboard to continue.
- Press the "Esc" button on the USB keyboard to cancel the current operation.
Step 16: Add Login to EEPROM
The Midbar (Teensy 4.1 Version) V3.0 offers 16 slots to store your login credentials in the EEPROM.
To add a login to the EEPROM using a USB keyboard:
- Select the "Logins In EEPROM" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Add" line;
- Press the "Enter" key on the USB keyboard;
- Choose the slot you want to put the login to by using the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard;
- Select the "USB Keyboard" line;
- Press the "Enter" key on the USB keyboard;
- Enter the username;
- Press the "Enter" key on the USB keyboard;
- Enter the password;
- Press the "Enter" key on the USB keyboard;
- Enter the website;
- Press the "Enter" key on the USB keyboard.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
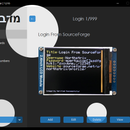
Step 17: View Login From EEPROM
To view a login from the EEPROM:
- Select the "Logins In EEPROM" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "View" line;
- Press the "Enter" key on the USB keyboard;
- Choose the slot you want to view login from by using the arrow keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 18: Type Login From EEPROM
The type feature allows you to use the Midbar (Teensy 4.1 Version) V3.0 as a USB keyboard. In other words, this version of Midbar can input your data to the computer as if you were typing it on a USB keyboard connected to your computer.
To type a login from the EEPROM:
- Select the "Logins In EEPROM" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Type" line;
- Press the "Enter" key on the USB keyboard;
- Choose the slot you want to type login from by using the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to type the website;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to type the username;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to type the password.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
*Flower pattern was generated by Bing Image Creator on December 17th, 2023.
Step 19: Delete Login From EEPROM
To delete a login from the EEPROM:
- Select the "Logins In EEPROM" line;
- Press the "Enter" key on the USB keyboard;
- Select the "Delete" line;
- Press the "Enter" key on the USB keyboard;
- Select the login you would like to delete by using the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard.
Step 20: Add Login to SD Card
With the Midbar (Teensy 4.1 Version) V3.0, you can store as many records on the SD card as you wish, as long as there is enough space on it.
Each record stored on an SD card has its own encrypted (verification) tag and a unique IV for each field.
To add a login to the SD card using the USB keyboard:
- Select the "Logins On SD Card" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Add" line;
- Press the "Enter" key on the USB keyboard;
- Choose the slot you want to put the login to by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard;
- Select the "USB Keyboard" line;
- Press the "Enter" key on the USB keyboard;
- Enter the title;
- Press the "Enter" key on the USB keyboard;
- Enter the username;
- Press the "Enter" key on the USB keyboard;
- Enter the password;
- Press the "Enter" key on the USB keyboard;
- Enter the website;
- Press the "Enter" key on the USB keyboard.
Based on the tests I've conducted, the Teensy 4.1 is capable of encrypting and decrypting a string of 10 000 characters using the 3DES + AES + Blowfish + Serpent encryption algorithm in CBC mode. Technically, you can put 10 000 characters into a field of a record.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 21: View Login From SD Card
To view a login from the SD card:
- Select the "Logins On SD Card" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "View" line;
- Press the "Enter" key on the USB keyboard;
- Choose the slot you want to view login from by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to print the record to the serial terminal. Note that this feature isn't available for the data stored in the EEPROM.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 22: Edit Login Stored on SD Card
To edit a login stored on the SD card:
- Select the "Logins On SD Card" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Edit" line;
- Press the "Enter" key on the USB keyboard;
- Select the login you would like to by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard;
- Select the input source;
- Press the "Enter" key on the USB keyboard;
- Depending on the chosen input source, either enter the new password you'd like to set on the USB keyboard or paste it to the Serial Terminal;
- Depending on the chosen input source, either press the "Enter" key on the USB keyboard or press the "Send" button in the Serial Terminal.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 23: Type Login From SD Card
To type a login from the SD card:
- Select the "Logins On SD Card" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Type" line;
- Press the "Enter" key on the USB keyboard;
- Choose the slot you want to type login from by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to type the website;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to type the username;
- Press the "↑" (Upwards Arrow) key on the USB keyboard to type the password.
*All credentials demonstrated here are entirely fictitious. Any similarity to actual credentials is purely coincidental.
Step 24: Delete Login From SD Card
To delete a login from the SD card:
- Select the "Logins On SD Card" line;
- Press the "Enter" key on the USB keyboard;
- Select the "Delete" line;
- Press the "Enter" key on the USB keyboard;
- Select the login you would like to delete by pressing the "←" (Leftwards Arrow) and "→" (Rightwards Arrow) keys on the USB keyboard;
- Press the "Enter" key on the USB keyboard.
The process of working with records of other types is very similar to the process of working with logins. And by the way, the "Type" feature works for all records stored on an SD card regardless of their type.
Step 25: Encrypt String
The Midbar (Teensy 4.1 Version) V3.0 utilizes seven encryption algorithms. You can use any of them to encrypt your data.
To encrypt string:
- Open the Serial Terminal (because the ciphertext is printed to it);
- Select the "Encryption Algorithms" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the line with the name of the encryption algorithm you would like to use;
- Press the "Enter" key on the USB keyboard;
- Select the "Encrypt String" line;
- Choose the input source;
- Press the "Enter" key on the USB keyboard;
- Depending on the chosen input source, either enter the text you'd like to encrypt on the USB keyboard or paste it to the Serial Terminal;
- Depending on the chosen input source, either press the "Enter" key on the USB keyboard or press the "Send" button in the Serial Terminal.
Step 26: Decrypt String
To decrypt string:
- Open the Serial Terminal (because you'll need to paste the ciphertext to it);
- Select the "Encryption Algorithms" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the line with the name of the encryption algorithm you've used to encrypt the text;
- Press the "Enter" key on the USB keyboard;
- Select the "Decrypt String" line;
- Choose where to display the decrypted string;
- Press the "Enter" key on the USB keyboard;
- Paste the ciphertext to the Serial Terminal;
- Press the "Send" button in the Serial Terminal.
Step 27: Back Up Data From EEPROM
Another handy feature of this version of Midbar is its ability to easily back up the EEPROM data to the Serial Terminal or the SD card.
To back up the EEPROM data to the SD card:
- Select the "Other Options" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Back Up Data From EEPROM" line;
- Press the "Enter" key on the USB keyboard;
- Select the "SD Card" line;
- Press the "Enter" key on the USB keyboard.
After you back up the EEPROM data to the SD card, the "Midback" file should appear there.
*Note that the factory reset will also erase the backup of the EEPROM data from the SD card.
Step 28: Restore Data to EEPROM
You can restore the EEPROM data from the SD card or the Serial Terminal.
To restore data to the EEPROM from the SD card:
- Select the "Other Options" line in the main menu;
- Press the "Enter" key on the USB keyboard;
- Select the "Restore Data To EEPROM" line;
- Press the "Enter" key on the USB keyboard;
- Select the "SD Card" line;
- Press the "Enter" key on the USB keyboard.
Step 29: Read an Encrypted Book and Encrypt Data Using Your Key
Midbar (Teensy 4.1 Version) V3.0 also enables you to read encrypted books and encrypt the data using your key.
You can read about it at https://www.instructables.com/How-to-Read-Encrypted-Books-and-Encrypt-Strings-Us/
Step 30: Find a Good Use for Midbar
Midbar's development process can often feel like taking three steps forward, and one step back, while also taking ten steps to the side.
However, despite its meandering path, Midbar is slowly taking shape with each passing version. On the upside though, this approach provides the opportunity to create multiple branches of Midbar, each with its own unique features, giving you a wide range of options to choose from.
And while Midbar is no guarantee of world peace or social harmony, I do believe that it's an important contribution to the protection of your data from unauthorized access.
I think it's also worth mentioning that Midbar's source code is distributed under the MIT license. That grants you the freedom to customize, adapt, and modify Midbar according to your needs and preferences. In other words, you can create your own version of Midbar or use it as a starting point for building new projects without the need for external permission.
If you found this tutorial to be useful, please consider sharing it.
Thank you for reading this tutorial.